Wallet Permissions
Introduction
OpenMask is built on the last stack and implements the latest version of chrome applications manifest - version 3. The major difference with manifest 2 is that service worker could not be persistent anymore. For applications in manifest 2 developers can run persistent worker and store critical and sensitive information in the memory store, the most secure store.
As an example MetaMask could be considered, it stores the password the way described. All wallet keys are encrypted and to decrypt the application has to know the password.
Why the focus is on version 3, which recently Google announced? The main reason is that the option allows running the persistent worker in the background would be removed. Google is going to stop supporting applications built with manifest 2 in 2023.
With manifest 3 developers can implement extensions with an interruptible service worker. The application background script would be aborted after 5 minutes of inactivity. The application no longer stores passwords from the wallet in a memory store.
However, OpenMask avoids asking users to fill in the password every 5 minutes. It was reached by different core permissions implementaion to read information from the wallet. The application provides an opportunity for the user to choose permissions options: allow or disallow dApp to read information from the locked wallet.
Core Permissions
The wallet save permission for every dApp during the first ton_requestAccounts request.
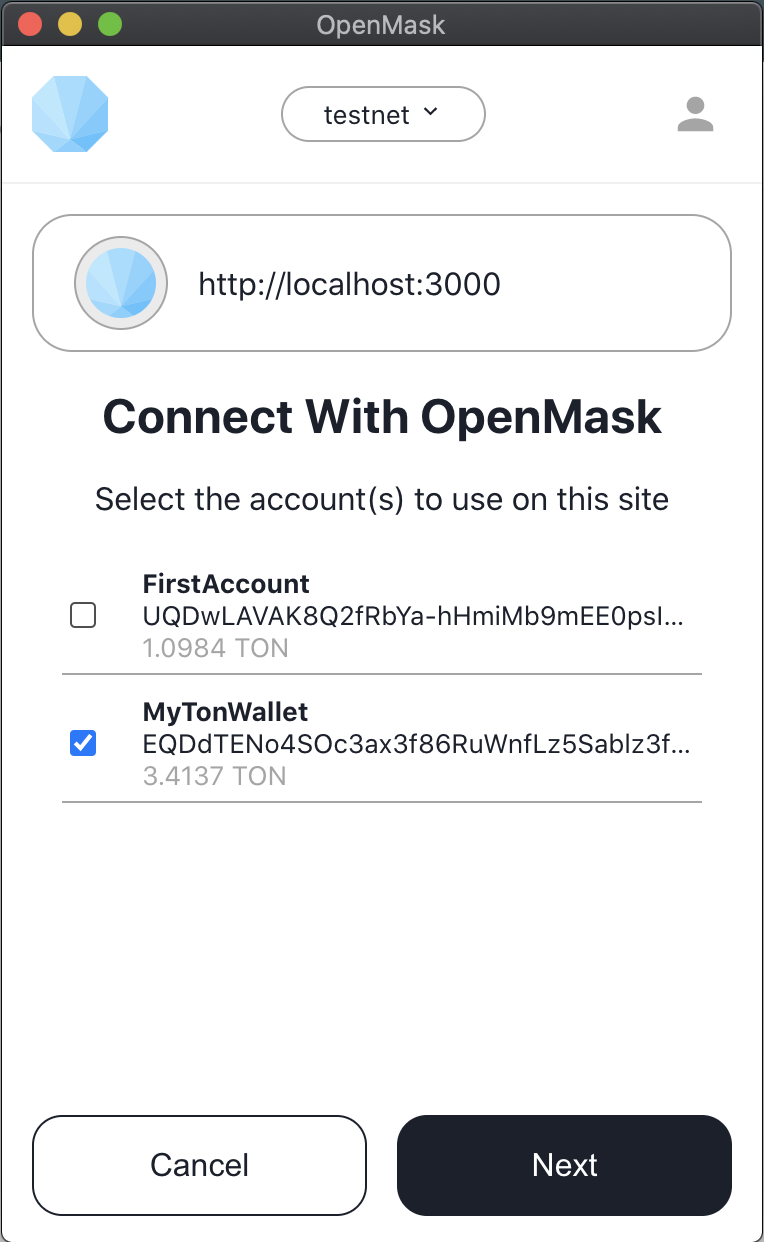
On the first connection, the owner sees a notification, and selects a wallet account to open and a permissions list to confirm it.
Base
Bese permission allows seeing the address, account balance, and activity for the unlocked wallet.
When the user would return to dApp and try to create a connection with the wallet by ton_requestAccounts request, he would see a notification to unlock the wallet.
Locked
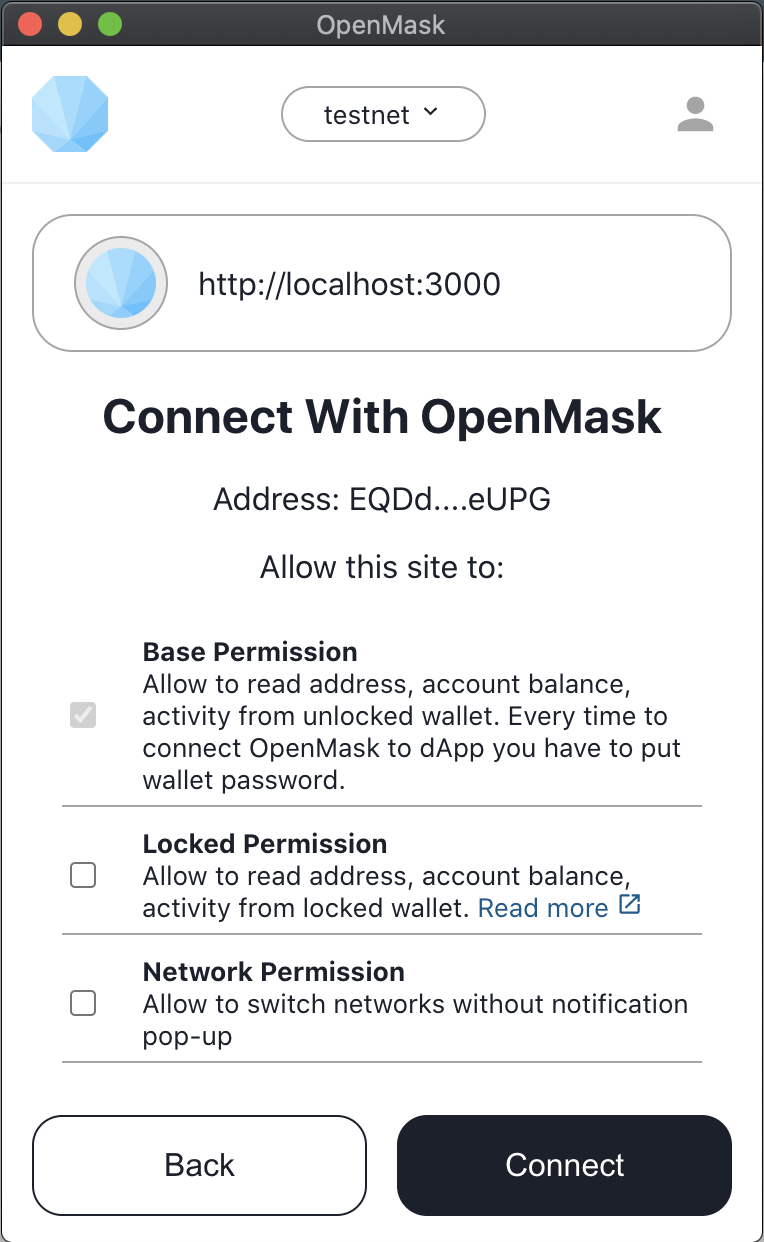
Locked permission allows to see the address, account balance, and activity for the locked wallet.
When the user would return to dApp the dApp could automatically create a connection and receive information by ton_requestAccounts request.
For both Base and Locked permission dApp could suggest a transaction. To confirm the transaction the owner have to unlock the wallet.
Additional Permissions
Network
Network permission allows dApp to switch wallet network without confirmation notification.